我在kubernetes集群中部署了emqx5.3版本的集群,在配置双向认证的功能上一直不能通过,困扰了我2天多的时间。
1、emqx服务端配置的是商业证书+自签的ca证书,mqttx客户端测试使用的是商业的ca证书+自签的client证书,一直不能验证通过;
2、如果我2端都使用商业证书就能验证通过,看起来问题貌似出在自签证书上面;
3、但是自签证书我们使用nginx实现双向认证配置代理的情况下是一切正常的,证明自签证书应该也没有问题。
我已经找不到突破口了,还请社区技术大牛支持,感激不尽!
在MQTTX 的设置里面把 SSL Secure 关了试一试
您好,感谢回复
我尝试过把SSL Secure关掉也不行,服务端我在监听器中把“没有证书则 SSL 失败”设置为“true”,也就是必须校验客户端证书,所有MQTTX客户端这边应该不能关掉SSL Secure吧?
那应该还是你的证书问题,你是混用自签和商业证书么?
对的,混用的,客户端校验服务端的是商业证书,服务端校验客户端的是自签证书,但是自签的那一套证书在nginx上使用是没有问题的,我也怀疑过是自签证书的问题,但是不知道是啥问题
另外说明一下,自签的有一个中间证书,根证书校验中间证书,中间证书校验客户端证书
问题不是自签证书,问题是混用,你开了双向认证,客户端和服务器的公钥签出用的不是同一个 CA 证书,证书校验应该是过不了的。你只用商业证书,或者只有自签证书应该是可以的
这里必须要求是同一个ca签发的证书吗?nginx上配置的话是没有这个限制的
不是,但是你需要确保客户端的 ca 证书可以成功校验 EMQX 的证书,同时在 EMQX 上设置的 ca 证书也需要能够校验客户端握手时携带的证书。
建议先找个证书校验的软件试一试
![]()
这个是商业证书校验
![]()
这个是自签证书校验
使用openssl工具校验,证书是没有问题的
2023-11-02T07:28:05.664228+00:00 [error] State machine <0.11238.6> terminating. Reason: {badmatch,{error,{asn1,{{wrong_tag,{{expected,19},{got,12,{12,<<“CN=SHANGHAITEST”>>}}}},[{‘OTP-PUB-KEY’,match_tags,2,[{file,“…/src/OTP-PUB-KEY.erl”},{line,24000}]},{‘OTP-PUB-KEY’,match_and_collect,2,[{file,“…/src/OTP-PUB-KEY.erl”},{line,23981}]},{‘OTP-PUB-KEY’,dec_X520SerialNumber,2,[{file,“…/src/OTP-PUB-KEY.erl”},{line,15800}]},{‘OTP-PUB-KEY’,decode,2,[{file,“…/src/OTP-PUB-KEY.erl”},{line,1233}]},{pubkey_cert_records,transform,2,[{file,“pubkey_cert_records.erl”},{line,80}]},{lists,map,2,[{file,“lists.erl”},{line,1315}]},{lists,map_1,2,[{file,“lists.erl”},{line,1320}]},{lists,map_1,2,[{file,“lists.erl”},{line,1320}]},{lists,map,2,[{file,“lists.erl”},{line,1315}]},{pubkey_cert_records,transform,2,[{file,“pubkey_cert_records.erl”},{line,92}]},{pubkey_cert_records,decode_tbs,1,[{file,“pubkey_cert_records.erl”},{line,331}]},{pubkey_cert_records,decode_cert,1,[{file,“pubkey_cert_records.erl”},{line,42}]},{public_key,pkix_decode_cert,2,[{file,“public_key.erl”},{line,521}]},{public_key,pkix_subject_id,1,[{file,“public_key.erl”},{line,1104}]},{tls_handshake_1_3,split_cert_entries,4,[{file,“tls_handshake_1_3.erl”},{line,1554}]},{tls_handshake_1_3,validate_certificate_chain,8,[{file,“tls_handshake_1_3.erl”},{line,1533}]},{tls_handshake_1_3,process_certificate,2,[{file,“tls_handshake_1_3.erl”},{line,1509}]},{tls_handshake_1_3,do_wait_cert,2,[{file,“tls_handshake_1_3.erl”},{line,933}]},{tls_connection_1_3,wait_cert,3,[{file,“tls_connection_1_3.erl”},{line,372}]},{gen_statem,loop_state_callback,11,[{file,“gen_statem.erl”},{line,1426}]},{tls_connection,init,1,[{file,“tls_connection.erl”},{line,160}]},{proc_lib,init_p_do_apply,3,[{file,“proc_lib.erl”},{line,240}]}]}}}}. Stack: [{public_key,pkix_decode_cert,2,[{file,“public_key.erl”},{line,525}]},{public_key,pkix_subject_id,1,[{file,“public_key.erl”},{line,1104}]},{tls_handshake_1_3,split_cert_entries,4,[{file,“tls_handshake_1_3.erl”},{line,1554}]},{tls_handshake_1_3,validate_certificate_chain,8,[{file,“tls_handshake_1_3.erl”},{line,1533}]},{tls_handshake_1_3,process_certificate,2,[{file,“tls_handshake_1_3.erl”},{line,1509}]},{tls_handshake_1_3,do_wait_cert,2,[{file,“tls_handshake_1_3.erl”},{line,933}]},{tls_connection_1_3,wait_cert,3,[{file,“tls_connection_1_3.erl”},{line,372}]},{gen_statem,loop_state_callback,11,[{file,“gen_statem.erl”},{line,1426}]},{tls_connection,init,1,[{file,“tls_connection.erl”},{line,160}]},{proc_lib,init_p_do_apply,3,[{file,“proc_lib.erl”},{line,240}]}]. Last event: {internal,{certificate_1_3,<<>>,[{certificate_entry,<<48,130,4,47,48,130,3,23,160,3,2,1,2,2,8,94,15,250,140,235,105,162,116,48,13,6,9,42,134,72,134,247,13,1,1,11,5,0,48,129,155,49,11,48,9,6,3,85,4,6,12,2,83,71,49,35,48,33,6,9,42,134,72,134,247,13,1,9,1,12,20,99,121,98,101,114,115,101,99,117,114,105,116,121,64,103,119,109,46,99,110,…>>,#{}}]}}. State: [{data,[{“State”,{wait_cert,{state,{static_env,server,gen_tcp,tls_gen_connection,tcp,tcp_closed,tcp_error,tcp_passive,“localhost”,8883,#Port<0.112402>,#Ref<0.1386437208.257818625.92162>,no_longer_defined,ssl_server_session_cache_db,{ssl_crl_cache,{{#Ref<0.1386437208.257818625.92165>,#Ref<0.1386437208.257818625.92166>},}},{#Ref<0.1386437208.257818625.92163>,#Ref<0.1386437208.257818625.92164>},#Ref<0.1386437208.256901122.252102>,[{session_id_tracker,<0.3550.0>}]},““,#{ciphers => [<<19,2>>,<<19,1>>,<<19,3>>,<<19,4>>,<<19,5>>,<<”>,<<“>,<<”>,<<“>,<<”>,<<“>,<<”>,<<“>,<<0,163>>,<<0,106>>,<<0,157>>,<<0,61>>,<<”>,<<“>,<<”>,<<“>,<<”>,<<“>,<<”>,<<“>,<<0,162>>,<<0,64>>,<<0,156>>,<<0,60>>,<<”>>,<<192,20>>,<<0,56>>,<<192,5>>,<<192,15>>,<<">>,<<192,19>>,<<0,50>>,<<192,4>>,<<192,14>>,<<0,173>>,<<0,183>>,<<0,172>>,<<0,182>>,<<0,149>>,<<0,148>>],eccs => {elliptic_curves,[{1,3,132,0,39},{1,3,132,0,38},{1,3,132,0,35},{1,3,36,3,3,2,8,1,1,13},{1,3,132,0,36},{1,3,132,0,37},{1,3,36,3,3,2,8,1,1,11},{1,3,132,0,34},{1,3,132,0,16},{1,3,132,0,17},{1,3,36,3,3,2,8,1,1,7},{1,3,132,0,10},{1,2,840,10045,3,1,7},{1,3,132,0,3},{1,3,132,0,26},{1,3,132,0,27},{1,3,132,0,32},{1,3,132,0,33},{1,3,132,0,24},{1,3,132,0,25},{1,3,132,0,31},{1,2,840,10045,3,1,1},{1,3,132,0,1},{1,3,132,0,2},{1,3,132,0,15},{1,3,132,0,9},{1,3,132,0,8},{1,3,132,0,30}]},receiver_spawn_opts => [],next_protocol_selector => undefined,use_ticket => undefined,certificate_authorities => true,max_handshake_size => 262144,erl_dist => false,early_data => undefined,certfile => <<“data/certs/listeners/ssl/default/cert-E99B78808FA20C05”>>,sni_hosts => [],max_fragment_length => undefined,verify => verify_peer,fail_if_no_peer_cert => true,reuse_sessions => true,cert => "”,alpn_advertised_protocols => undefined,cacerts => “",ocsp_nonce => true,ocsp_stapling => false,user_lookup_fun => {fun emqx_tls_psk:lookup/3,undefined},sni_fun => undefined,hibernate_after => 5000,anti_replay => undefined,signature_algs_cert => undefined,session_tickets => disabled,customize_hostname_check => [],middlebox_comp_mode => true,partial_chain => #Fun<ssl.11.97316091>,keep_secrets => false,reuse_session => #Fun<ssl.13.97316091>,dh => "”,password => ““,log_level => notice,cacertfile => <<”/opt/emqx/data/certs/listeners/ssl/default/cacert-1FD942C7112241E6">>,versions => [{3,4},{3,3},{3,2},{3,1}],fallback => undefined,key => "”,honor_ecc_order => false,padding_check => true,psk_identity => “",alpn_preferred_protocols => undefined,renegotiate_at => 268435456,protocol => tls,server_name_indication => undefined,keyfile => <<“data/certs/listeners/ssl/default/key-362ABF5B8602ABC8”>>,cookie => true,client_renegotiation => true,ocsp_responder_certs => [],srp_identity => "”,dhfile => undefined,supported_groups => {supported_groups,[x25519,x448,secp256r1,secp384r1]},crl_check => false,verify_fun => undefined,certificate_status => undefined,handshake => full,sender_spawn_opts => ,depth => 10,signature_algs => [eddsa_ed25519,eddsa_ed448,ecdsa_secp521r1_sha512,ecdsa_secp384r1_sha384,ecdsa_secp256r1_sha256,rsa_pss_pss_sha512,rsa_pss_pss_sha384,rsa_pss_pss_sha256,rsa_pss_rsae_sha512,rsa_pss_rsae_sha384,rsa_pss_rsae_sha256,{sha512,ecdsa},{sha512,rsa},{sha384,ecdsa},{sha384,rsa},{sha256,ecdsa},{sha256,rsa},{sha224,ecdsa},{sha224,rsa},{sha,ecdsa},{sha,rsa},{sha,dsa}],next_protocols_advertised => undefined,honor_cipher_order => true,secure_renegotiate => true,crl_cache => {ssl_crl_cache,{internal,}},key_update_at => 388736063997,beast_mitigation => one_n_minus_one},{socket_options,binary,0,0,0,false},““,””,not_requested,#{active_n => 100,active_n_toggle => false,change_cipher_spec => fail,sender => <0.11237.6>,status_request => undefined},““,{key_share_server_hello,{key_share_entry,x25519,{<<114,5,241,37,141,206,27,104,212,85,99,86,28,74,184,112,116,42,58,109,55,58,34,132,64,174,153,231,27,230,33,72>>,<<216,209,167,216,52,170,103,114,162,156,49,14,224,1,176,87,70,171,180,92,126,253,221,95,54,94,81,179,148,132,223,71>>}}},””,““,””,undefined,{<0.11234.6>,#Ref<0.1386437208.258473985.185795>},undefined}}}]}].
2023-11-02T07:28:05.666355+00:00 [error] crasher: initial call: ssl_gen_statem:init/1, pid: <0.11238.6>, registered_name: , error: {{badmatch,{error,{asn1,{{wrong_tag,{{expected,19},{got,12,{12,<<“CN=SHANGHAITEST”>>}}}},[{‘OTP-PUB-KEY’,match_tags,2,[{file,“…/src/OTP-PUB-KEY.erl”},{line,24000}]},{‘OTP-PUB-KEY’,match_and_collect,2,[{file,“…/src/OTP-PUB-KEY.erl”},{line,23981}]},{‘OTP-PUB-KEY’,dec_X520SerialNumber,2,[{file,“…/src/OTP-PUB-KEY.erl”},{line,15800}]},{‘OTP-PUB-KEY’,decode,2,[{file,“…/src/OTP-PUB-KEY.erl”},{line,1233}]},{pubkey_cert_records,transform,2,[{file,“pubkey_cert_records.erl”},{line,80}]},{lists,map,2,[{file,“lists.erl”},{line,1315}]},{lists,map_1,2,[{file,“lists.erl”},{line,1320}]},{lists,map_1,2,[{file,“lists.erl”},{line,1320}]},{lists,map,2,[{file,“lists.erl”},{line,1315}]},{pubkey_cert_records,transform,2,[{file,“pubkey_cert_records.erl”},{line,92}]},{pubkey_cert_records,decode_tbs,1,[{file,“pubkey_cert_records.erl”},{line,331}]},{pubkey_cert_records,decode_cert,1,[{file,“pubkey_cert_records.erl”},{line,42}]},{public_key,pkix_decode_cert,2,[{file,“public_key.erl”},{line,521}]},{public_key,pkix_subject_id,1,[{file,“public_key.erl”},{line,1104}]},{tls_handshake_1_3,split_cert_entries,4,[{file,“tls_handshake_1_3.erl”},{line,1554}]},{tls_handshake_1_3,validate_certificate_chain,8,[{file,“tls_handshake_1_3.erl”},{line,1533}]},{tls_handshake_1_3,process_certificate,2,[{file,“tls_handshake_1_3.erl”},{line,1509}]},{tls_handshake_1_3,do_wait_cert,2,[{file,“tls_handshake_1_3.erl”},{line,933}]},{tls_connection_1_3,wait_cert,3,[{file,“tls_connection_1_3.erl”},{line,372}]},{gen_statem,loop_state_callback,11,[{file,“gen_statem.erl”},{line,1426}]},{tls_connection,init,1,[{file,“tls_connection.erl”},{line,160}]},{proc_lib,init_p_do_apply,3,[{file,“proc_lib.erl”},{line,240}]}]}}}},[{public_key,pkix_decode_cert,2,[{file,“public_key.erl”},{line,525}]},{public_key,pkix_subject_id,1,[{file,“public_key.erl”},{line,1104}]},{tls_handshake_1_3,split_cert_entries,4,[{file,“tls_handshake_1_3.erl”},{line,1554}]},{tls_handshake_1_3,validate_certificate_chain,8,[{file,“tls_handshake_1_3.erl”},{line,1533}]},{tls_handshake_1_3,process_certificate,2,[{file,“tls_handshake_1_3.erl”},{line,1509}]},{tls_handshake_1_3,do_wait_cert,2,[{file,“tls_handshake_1_3.erl”},{line,933}]},{tls_connection_1_3,wait_cert,3,[{file,“tls_connection_1_3.erl”},{line,372}]},{gen_statem,loop_state_callback,11,[{file,“gen_statem.erl”},{line,1426}]},{tls_connection,init,1,[{file,“tls_connection.erl”},{line,160}]},{proc_lib,init_p_do_apply,3,[{file,“proc_lib.erl”},{line,240}]}]}, ancestors: [<0.11236.6>,tls_connection_sup,tls_sup,ssl_connection_sup,ssl_sup,<0.2052.0>], message_queue_len: 0, messages: , links: [<0.11236.6>], dictionary: [{log_level,notice},{ssl_pem_cache,ssl_pem_cache},{ssl_manager,ssl_manager}], trap_exit: true, status: running, heap_size: 46422, stack_size: 28, reductions: 73483; neighbours:
2023-11-02T07:28:05.667214+00:00 [error] supervisor: {esockd_connection_sup,<0.11234.6>}, errorContext: connection_shutdown, reason: {ssl_failure,{{{badmatch,{error,{asn1,{{wrong_tag,{{expected,19},{got,12,{12,<<“CN=SHANGHAITEST”>>}}}},[{‘OTP-PUB-KEY’,match_tags,2,[{file,“…/src/OTP-PUB-KEY.erl”},{line,24000}]},{‘OTP-PUB-KEY’,match_and_collect,2,[{file,“…/src/OTP-PUB-KEY.erl”},{line,23981}]},{‘OTP-PUB-KEY’,dec_X520SerialNumber,2,[{file,“…/src/OTP-PUB-KEY.erl”},{line,15800}]},{‘OTP-PUB-KEY’,decode,2,[{file,“…/src/OTP-PUB-KEY.erl”},{line,1233}]},{pubkey_cert_records,transform,2,[{file,“pubkey_cert_records.erl”},{line,80}]},{lists,map,2,[{file,“lists.erl”},{line,1315}]},{lists,map_1,2,[{file,“lists.erl”},{line,1320}]},{lists,map_1,2,[{file,“lists.erl”},{line,1320}]},{lists,map,2,[{file,“lists.erl”},{line,1315}]},{pubkey_cert_records,transform,2,[{file,“pubkey_cert_records.erl”},{line,92}]},{pubkey_cert_records,decode_tbs,1,[{file,“pubkey_cert_records.erl”},{line,331}]},{pubkey_cert_records,decode_cert,1,[{file,“pubkey_cert_records.erl”},{line,42}]},{public_key,pkix_decode_cert,2,[{file,“public_key.erl”},{line,521}]},{public_key,pkix_subject_id,1,[{file,“public_key.erl”},{line,1104}]},{tls_handshake_1_3,split_cert_entries,4,[{file,“tls_handshake_1_3.erl”},{line,1554}]},{tls_handshake_1_3,validate_certificate_chain,8,[{file,“tls_handshake_1_3.erl”},{line,1533}]},{tls_handshake_1_3,process_certificate,2,[{file,“tls_handshake_1_3.erl”},{line,1509}]},{tls_handshake_1_3,do_wait_cert,2,[{file,“tls_handshake_1_3.erl”},{line,933}]},{tls_connection_1_3,wait_cert,3,[{file,“tls_connection_1_3.erl”},{line,372}]},{gen_statem,loop_state_callback,11,[{file,“gen_statem.erl”},{line,1426}]},{tls_connection,init,1,[{file,“tls_connection.erl”},{line,160}]},{proc_lib,init_p_do_apply,3,[{file,“proc_lib.erl”},{line,240}]}]}}}},[{public_key,pkix_decode_cert,2,[{file,“public_key.erl”},{line,525}]},{public_key,pkix_subject_id,1,[{file,“public_key.erl”},{line,1104}]},{tls_handshake_1_3,split_cert_entries,4,[{file,“tls_handshake_1_3.erl”},{line,1554}]},{tls_handshake_1_3,validate_certificate_chain,8,[{file,“tls_handshake_1_3.erl”},{line,1533}]},{tls_handshake_1_3,process_certificate,2,[{file,“tls_handshake_1_3.erl”},{line,1509}]},{tls_handshake_1_3,do_wait_cert,2,[{file,“tls_handshake_1_3.erl”},{line,933}]},{tls_connection_1_3,wait_cert,3,[{file,“tls_connection_1_3.erl”},{line,372}]},{gen_statem,loop_state_callback,11,[{file,“gen_statem.erl”},{line,1426}]},{tls_connection,init,1,[{file,“tls_connection.erl”},{line,160}]},{proc_lib,init_p_do_apply,3,[{file,“proc_lib.erl”},{line,240}]}]},{gen_statem,call,[<0.11238.6>,{start,15000},infinity]}}}, offender: [{pid,<0.11234.6>},{name,connection},{mfargs,{emqx_connection,start_link,[#{enable_authn => true,limiter => undefined,listener => {ssl,default},zone => default}]}}]
2023-11-02T07:28:05.667189+00:00 [error] Supervisor: {<0.11236.6>,tls_dyn_connection_sup}. Context: child_terminated. Reason: {{badmatch,{error,{asn1,{{wrong_tag,{{expected,19},{got,12,{12,<<“CN=SHANGHAITEST”>>}}}},[{‘OTP-PUB-KEY’,match_tags,2,[{file,“…/src/OTP-PUB-KEY.erl”},{line,24000}]},{‘OTP-PUB-KEY’,match_and_collect,2,[{file,“…/src/OTP-PUB-KEY.erl”},{line,23981}]},{‘OTP-PUB-KEY’,dec_X520SerialNumber,2,[{file,“…/src/OTP-PUB-KEY.erl”},{line,15800}]},{‘OTP-PUB-KEY’,decode,2,[{file,“…/src/OTP-PUB-KEY.erl”},{line,1233}]},{pubkey_cert_records,transform,2,[{file,“pubkey_cert_records.erl”},{line,80}]},{lists,map,2,[{file,“lists.erl”},{line,1315}]},{lists,map_1,2,[{file,“lists.erl”},{line,1320}]},{lists,map_1,2,[{file,“lists.erl”},{line,1320}]},{lists,map,2,[{file,“lists.erl”},{line,1315}]},{pubkey_cert_records,transform,2,[{file,“pubkey_cert_records.erl”},{line,92}]},{pubkey_cert_records,decode_tbs,1,[{file,“pubkey_cert_records.erl”},{line,331}]},{pubkey_cert_records,decode_cert,1,[{file,“pubkey_cert_records.erl”},{line,42}]},{public_key,pkix_decode_cert,2,[{file,“public_key.erl”},{line,521}]},{public_key,pkix_subject_id,1,[{file,“public_key.erl”},{line,1104}]},{tls_handshake_1_3,split_cert_entries,4,[{file,“tls_handshake_1_3.erl”},{line,1554}]},{tls_handshake_1_3,validate_certificate_chain,8,[{file,“tls_handshake_1_3.erl”},{line,1533}]},{tls_handshake_1_3,process_certificate,2,[{file,“tls_handshake_1_3.erl”},{line,1509}]},{tls_handshake_1_3,do_wait_cert,2,[{file,“tls_handshake_1_3.erl”},{line,933}]},{tls_connection_1_3,wait_cert,3,[{file,“tls_connection_1_3.erl”},{line,372}]},{gen_statem,loop_state_callback,11,[{file,“gen_statem.erl”},{line,1426}]},{tls_connection,init,1,[{file,“tls_connection.erl”},{line,160}]},{proc_lib,init_p_do_apply,3,[{file,“proc_lib.erl”},{line,240}]}]}}}},[{public_key,pkix_decode_cert,2,[{file,“public_key.erl”},{line,525}]},{public_key,pkix_subject_id,1,[{file,“public_key.erl”},{line,1104}]},{tls_handshake_1_3,split_cert_entries,4,[{file,“tls_handshake_1_3.erl”},{line,1554}]},{tls_handshake_1_3,validate_certificate_chain,8,[{file,“tls_handshake_1_3.erl”},{line,1533}]},{tls_handshake_1_3,process_certificate,2,[{file,“tls_handshake_1_3.erl”},{line,1509}]},{tls_handshake_1_3,do_wait_cert,2,[{file,“tls_handshake_1_3.erl”},{line,933}]},{tls_connection_1_3,wait_cert,3,[{file,“tls_connection_1_3.erl”},{line,372}]},{gen_statem,loop_state_callback,11,[{file,“gen_statem.erl”},{line,1426}]},{tls_connection,init,1,[{file,“tls_connection.erl”},{line,160}]},{proc_lib,init_p_do_apply,3,[{file,“proc_lib.erl”},{line,240}]}]}. Offender: id=receiver,pid=<0.11238.6>.
这个是emqx服务端的错误日志,看不懂
方便发送下客户端的 PEM 么,看起来是证书中有不被支持的扩展,我这边验证下
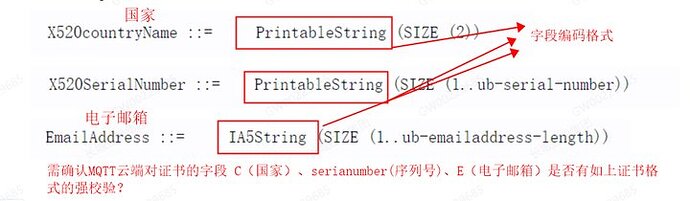
您好,我找了公司内部专业团队的协助,基本能确定是因为证书的原因,需要和您确认一下,证书中字段(contryName,SerialNumber,EmailAddress)的编码格式,EMQX服务端是否有强校验?据我所知,当前有问题的证书中这几个字段的编码格式是utf8