docker版本的emqx4.3.10
问题描述
按照社区的文章自签SSL证书,无法连接
配置文件及日志
listener.ssl.external.keyfile = etc/certs/emqx.key.pem
listener.ssl.external.certfile = etc/certs/emqx.pem
listener.ssl.external.cacertfile = etc/certs/ca.pem
listener.ssl.external.verify = verify_peer
listener.ssl.external.fail_if_no_peer_cert = true
以下是证书生成过程
- 生成CA私钥,私钥中包含了公钥
openssl genrsa -out ca.key 2048 - 生成CA自签名证书请求文件
openssl req -new -key ca.key -out ca.csr -subj "/C=CN/ST=Jiangxi/L=Nanchang/O=zlang/OU=EMQX/CN=*.xxx.net/emailAddress=xxx@sohu.com" - 生成CA自签名证书
openssl x509 -req -days 3650 -in ca.csr -signkey ca.key -CAcreateserial -out ca.pem - 生成服务器私钥
openssl genrsa -out emqx.key 2048 - 从私钥中提取出公钥
openssl rsa -in emqx.key -pubout -out server_public.key - 生成服务器证书请求文件
openssl req -new -key emqx.key -out server_req.csr -subj "/C=CN/ST=Jiangxi/L=Nanchang/O=zlang/OU=EMQX/CN=*.xxx.net/emailAddress=xxx@sohu.com" - 生成服务器证书
openssl x509 -req -days 3650 -in server_req.csr -CA ca.pem -CAkey ca.key -CAcreateserial -out emqx.pem - 生成客户端私钥
openssl genrsa -out client.key 2048 - 从私钥中提取出公钥
openssl rsa -in client.key -pubout -out client_public.key - 生成客户端证书请求文件
openssl req -new -key client.key -out client_req.csr -subj "/C=CN/ST=Jiangxi/L=Nanchang/O=zlang/OU=EMQX/CN=*.xxx.net/emailAddress=xxxx@sohu.com" - 生成客户端证书
openssl x509 -req -days 3650 -in client_req.csr -CA ca.pem -CAkey ca.key -CAcreateserial -out client.pem openssl s_client -connect localhost:2020 -cert client.pem -key client.key.pem openssl s_server -accept 2020 -key emqx.key.pem -cert emqx.pem
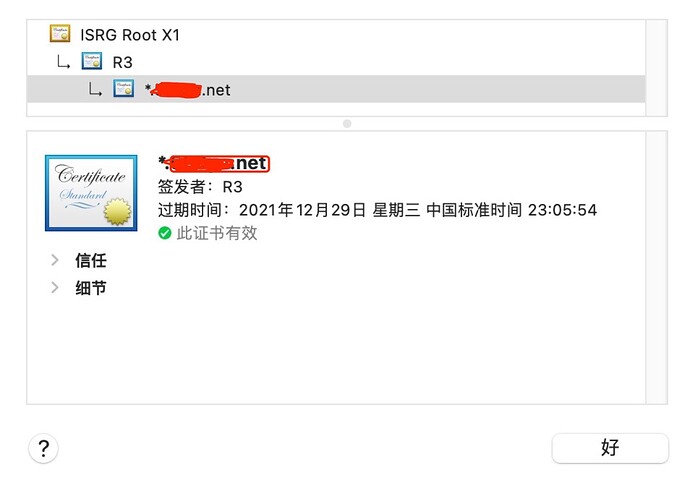
证书通过上述方法可以验证
Start Time: 1637651645
Timeout : 7200 (sec)
Verify return code: 18 (self signed certificate)
Extended master secret: no
Max Early Data: 0
MQTTX连接的报错日志:
[2021-11-23 14:27:07] [ERROR] Connect fail, MQTT.js onError trigger, Error: self signed certificate
at TLSSocket.onConnectSecure (_tls_wrap.js:1501:34)
at TLSSocket.emit (events.js:315:20)
at TLSSocket._finishInit (_tls_wrap.js:936:8)
at TLSWrap.ssl.onhandshakedone (_tls_wrap.js:710:12)
[2021-11-23 14:27:07] [INFO] Connect close, MQTT.js onClose trigger
[2021-11-23 14:50:26] [INFO] Connect client, MQTT/SSL connection: mqtts://192.168.1.13:8883
[2021-11-23 14:50:26] [INFO] MQTTX client with ID 8af17255-e0ff-4568-94ad-b824dcc3b3bd assigned
[2021-11-23 14:50:26] [ERROR] Connect fail, MQTT.js onError trigger, Error: self signed certificate
at TLSSocket.onConnectSecure (_tls_wrap.js:1501:34)
at TLSSocket.emit (events.js:315:20)
at TLSSocket._finishInit (_tls_wrap.js:936:8)
at TLSWrap.ssl.onhandshakedone (_tls_wrap.js:710:12)
[2021-11-23 14:50:26] [INFO] Connect close, MQTT.js onClose trigger
[2021-11-23 14:56:55] [INFO] Connect client, MQTT/SSL connection: mqtts://xxx.xxxx.net:8883
[2021-11-23 14:56:55] [INFO] MQTTX client with ID 8af17255-e0ff-4568-94ad-b824dcc3b3bd assigned
[2021-11-23 14:56:55] [ERROR] Connect fail, MQTT.js onError trigger, Error: self signed certificate
at TLSSocket.onConnectSecure (_tls_wrap.js:1501:34)
at TLSSocket.emit (events.js:315:20)
at TLSSocket._finishInit (_tls_wrap.js:936:8)
at TLSWrap.ssl.onhandshakedone (_tls_wrap.js:710:12)
MQTT.fx的报错日志
2021-11-23 14:51:44,130 INFO --- ScriptsController : Clear console.
2021-11-23 14:51:44,130 ERROR --- BrokerConnectService : MqttException
2021-11-23 14:56:29,455 INFO --- BrokerConnectorController : onConnect
2021-11-23 14:56:29,457 INFO --- ScriptsController : Clear console.
2021-11-23 14:56:29,458 INFO --- MqttFX ClientModel : MqttClient with ID 9a2dd7021eee43389d99c0572c1443fa assigned.
2021-11-23 14:56:29,508 ERROR --- MqttFX ClientModel : Error when connecting
org.eclipse.paho.client.mqttv3.MqttException: MqttException
at org.eclipse.paho.client.mqttv3.internal.ExceptionHelper.createMqttException(ExceptionHelper.java:38) ~[org.eclipse.paho.client.mqttv3-1.2.0.jar:?]
at org.eclipse.paho.client.mqttv3.internal.ClientComms$ConnectBG.run(ClientComms.java:715) ~[org.eclipse.paho.client.mqttv3-1.2.0.jar:?]
at java.util.concurrent.Executors$RunnableAdapter.call(Executors.java:511) ~[?:1.8.0_181]
at java.util.concurrent.FutureTask.run(FutureTask.java:266) ~[?:1.8.0_181]
at java.util.concurrent.ScheduledThreadPoolExecutor$ScheduledFutureTask.access$201(ScheduledThreadPoolExecutor.java:180) ~[?:1.8.0_181]
at java.util.concurrent.ScheduledThreadPoolExecutor$ScheduledFutureTask.run(ScheduledThreadPoolExecutor.java:293) ~[?:1.8.0_181]
at java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1149) [?:1.8.0_181]
at java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:624) [?:1.8.0_181]
at java.lang.Thread.run(Thread.java:748) [?:1.8.0_181]
Caused by: javax.net.ssl.SSLHandshakeException: Received fatal alert: bad_certificate
at sun.security.ssl.Alerts.getSSLException(Alerts.java:192) ~[?:1.8.0_181]
at sun.security.ssl.Alerts.getSSLException(Alerts.java:154) ~[?:1.8.0_181]
at sun.security.ssl.SSLSocketImpl.recvAlert(SSLSocketImpl.java:2038) ~[?:1.8.0_181]
at sun.security.ssl.SSLSocketImpl.readRecord(SSLSocketImpl.java:1135) ~[?:1.8.0_181]
at sun.security.ssl.SSLSocketImpl.performInitialHandshake(SSLSocketImpl.java:1385) ~[?:1.8.0_181]
at sun.security.ssl.SSLSocketImpl.startHandshake(SSLSocketImpl.java:1413) ~[?:1.8.0_181]
at sun.security.ssl.SSLSocketImpl.startHandshake(SSLSocketImpl.java:1397) ~[?:1.8.0_181]
at org.eclipse.paho.client.mqttv3.internal.SSLNetworkModule.start(SSLNetworkModule.java:108) ~[org.eclipse.paho.client.mqttv3-1.2.0.jar:?]
at org.eclipse.paho.client.mqttv3.internal.ClientComms$ConnectBG.run(ClientComms.java:701) ~[org.eclipse.paho.client.mqttv3-1.2.0.jar:?]
... 7 more
2021-11-23 14:56:29,509 ERROR --- MqttFX ClientModel : Please verify your Settings (e.g. Broker Address, Broker Port & Client ID) and the user credentials!
org.eclipse.paho.client.mqttv3.MqttException: MqttException
at org.eclipse.paho.client.mqttv3.internal.ExceptionHelper.createMqttException(ExceptionHelper.java:38) ~[org.eclipse.paho.client.mqttv3-1.2.0.jar:?]
at org.eclipse.paho.client.mqttv3.internal.ClientComms$ConnectBG.run(ClientComms.java:715) ~[org.eclipse.paho.client.mqttv3-1.2.0.jar:?]
at java.util.concurrent.Executors$RunnableAdapter.call(Executors.java:511) ~[?:1.8.0_181]
at java.util.concurrent.FutureTask.run(FutureTask.java:266) ~[?:1.8.0_181]
at java.util.concurrent.ScheduledThreadPoolExecutor$ScheduledFutureTask.access$201(ScheduledThreadPoolExecutor.java:180) ~[?:1.8.0_181]
at java.util.concurrent.ScheduledThreadPoolExecutor$ScheduledFutureTask.run(ScheduledThreadPoolExecutor.java:293) ~[?:1.8.0_181]
at java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1149) [?:1.8.0_181]
at java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:624) [?:1.8.0_181]
at java.lang.Thread.run(Thread.java:748) [?:1.8.0_181]
Caused by: javax.net.ssl.SSLHandshakeException: Received fatal alert: bad_certificate
at sun.security.ssl.Alerts.getSSLException(Alerts.java:192) ~[?:1.8.0_181]
at sun.security.ssl.Alerts.getSSLException(Alerts.java:154) ~[?:1.8.0_181]
at sun.security.ssl.SSLSocketImpl.recvAlert(SSLSocketImpl.java:2038) ~[?:1.8.0_181]
at sun.security.ssl.SSLSocketImpl.readRecord(SSLSocketImpl.java:1135) ~[?:1.8.0_181]
at sun.security.ssl.SSLSocketImpl.performInitialHandshake(SSLSocketImpl.java:1385) ~[?:1.8.0_181]
at sun.security.ssl.SSLSocketImpl.startHandshake(SSLSocketImpl.java:1413) ~[?:1.8.0_181]
at sun.security.ssl.SSLSocketImpl.startHandshake(SSLSocketImpl.java:1397) ~[?:1.8.0_181]
at org.eclipse.paho.client.mqttv3.internal.SSLNetworkModule.start(SSLNetworkModule.java:108) ~[org.eclipse.paho.client.mqttv3-1.2.0.jar:?]
at org.eclipse.paho.client.mqttv3.internal.ClientComms$ConnectBG.run(ClientComms.java:701) ~[org.eclipse.paho.client.mqttv3-1.2.0.jar:?]
... 7 more
2021-11-23 14:56:29,512 INFO --- ScriptsController : Clear console.
2021-11-23 14:56:29,512 ERROR --- BrokerConnectService : MqttException
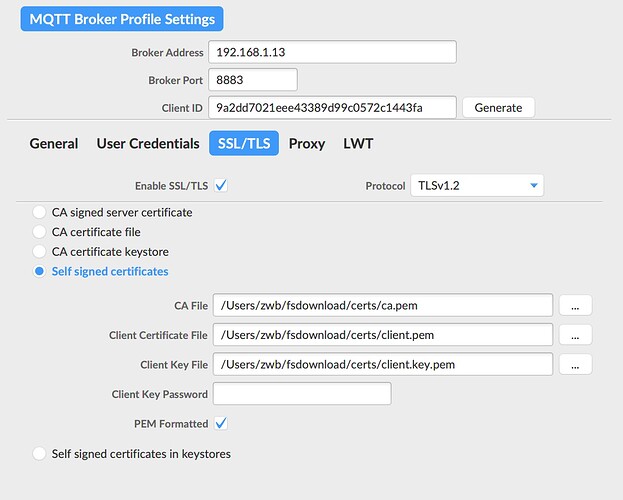
MQTT.fx的连接设置截图
另外,按照配置,我应该是开启了证书认证吧,但是用证书是无法连接的,不用证书反而连接上了。
在 emqx 的 docker 里面 log 的文件夹下面没有日志文件产生。
通过 docker logs 命令,得到如下日志:
Starting emqx on node b220f1fadae3@172.17.0.2
Start mqtt:tcp:internal listener on 127.0.0.1:11883 successfully.
Start mqtt:tcp:external listener on 0.0.0.0:1883 successfully.
Start mqtt:ws:external listener on 0.0.0.0:8083 successfully.
Start mqtt:ssl:external listener on 0.0.0.0:8883 successfully.
Start mqtt:wss:external listener on 0.0.0.0:8084 successfully.
Start http:management listener on 8081 successfully.
Start http:dashboard listener on 18083 successfully.
EMQ X Broker 4.3.10 is running now!
2021-11-23T14:51:07.238304+08:00 [error] supervisor: 'esockd_connection_sup - <0.1816.0>', errorContext: connection_shutdown, reason: {ssl_error,{tls_alert,{bad_certificate,"TLS server: In state certify at ssl_handshake.erl:1885 generated SERVER ALERT: Fatal - Bad Certificate\n"}}}, offender: [{pid,<0.2377.0>},{name,connection},{mfargs,{emqx_connection,start_link,[[{deflate_options,[]},{max_conn_rate,500},{active_n,100},{zone,external},{proxy_address_header,<<>>},{proxy_port_header,<<>>},{supported_subprotocols,[]}]]}}]
2021-11-23T14:51:07.253390+08:00 [error] supervisor: 'esockd_connection_sup - <0.1816.0>', errorContext: connection_shutdown, reason: {ssl_error,{tls_alert,{bad_certificate,"TLS server: In state certify at ssl_handshake.erl:1885 generated SERVER ALERT: Fatal - Bad Certificate\n"}}}, offender: [{pid,<0.2381.0>},{name,connection},{mfargs,{emqx_connection,start_link,[[{deflate_options,[]},{max_conn_rate,500},{active_n,100},{zone,external},{proxy_address_header,<<>>},{proxy_port_header,<<>>},{supported_subprotocols,[]}]]}}]
2021-11-23T14:51:44.208547+08:00 [error] supervisor: 'esockd_connection_sup - <0.1816.0>', errorContext: connection_shutdown, reason: {ssl_error,{tls_alert,{bad_certificate,"TLS server: In state certify at ssl_handshake.erl:1885 generated SERVER ALERT: Fatal - Bad Certificate\n"}}}, offender: [{pid,<0.2397.0>},{name,connection},{mfargs,{emqx_connection,start_link,[[{deflate_options,[]},{max_conn_rate,500},{active_n,100},{zone,external},{proxy_address_header,<<>>},{proxy_port_header,<<>>},{supported_subprotocols,[]}]]}}]
2021-11-23T14:56:29.592960+08:00 [error] supervisor: 'esockd_connection_sup - <0.1816.0>', errorContext: connection_shutdown, reason: {ssl_error,{tls_alert,{bad_certificate,"TLS server: In state certify at ssl_handshake.erl:1885 generated SERVER ALERT: Fatal - Bad Certificate\n"}}}, offender: [{pid,<0.2496.0>},{name,connection},{mfargs,{emqx_connection,start_link,[[{deflate_options,[]},{max_conn_rate,500},{active_n,100},{zone,external},{proxy_address_header,<<>>},{proxy_port_header,<<>>},{supported_subprotocols,[]}]]}}]
2021-11-23T14:57:35.769483+08:00 [error] supervisor: 'esockd_connection_sup - <0.1816.0>', errorContext: connection_shutdown, reason: {ssl_error,{tls_alert,{bad_certificate,"TLS server: In state wait_cert at ssl_handshake.erl:1885 generated SERVER ALERT: Fatal - Bad Certificate\n"}}}, offender: [{pid,<0.2512.0>},{name,connection},{mfargs,{emqx_connection,start_link,[[{deflate_options,[]},{max_conn_rate,500},{active_n,100},{zone,external},{proxy_address_header,<<>>},{proxy_port_header,<<>>},{supported_subprotocols,[]}]]}}]
2021-11-23T14:57:38.889707+08:00 [error] supervisor: 'esockd_connection_sup - <0.1816.0>', errorContext: connection_shutdown, reason: {ssl_error,{tls_alert,{bad_certificate,"TLS server: In state wait_cert at ssl_handshake.erl:1885 generated SERVER ALERT: Fatal - Bad Certificate\n"}}}, offender: [{pid,<0.2515.0>},{name,connection},{mfargs,{emqx_connection,start_link,[[{deflate_options,[]},{max_conn_rate,500},{active_n,100},{zone,external},{proxy_address_header,<<>>},{proxy_port_header,<<>>},{supported_subprotocols,[]}]]}}]
2021-11-23T14:57:39.661654+08:00 [error] supervisor: 'esockd_connection_sup - <0.1816.0>', errorContext: connection_shutdown, reason: {ssl_error,{tls_alert,{bad_certificate,"TLS server: In state wait_cert at ssl_handshake.erl:1885 generated SERVER ALERT: Fatal - Bad Certificate\n"}}}, offender: [{pid,<0.2518.0>},{name,connection},{mfargs,{emqx_connection,start_link,[[{deflate_options,[]},{max_conn_rate,500},{active_n,100},{zone,external},{proxy_address_header,<<>>},{proxy_port_header,<<>>},{supported_subprotocols,[]}]]}}]